Apple's 'Extremely Sophisticated Attack' Zero-Day: How Hackers Are Exploiting CVE-2025-43300
Apple's CVE-2025-43300 zero-day lets hackers compromise devices through malicious images. No downloads needed—just viewing weaponized images triggers device takeover. Affects 1.5B iPhones, iPads, and Macs. Advanced threat actors already exploiting in "sophisticated attacks" against targets.

Published: August 21, 2025 | 5 min read
Yesterday's emergency Apple patch revealed a zero-day vulnerability that security experts are calling "a hacker's dream." CVE-2025-43300 was actively exploited by advanced threat actors in what Apple describes as "extremely sophisticated attacks" against targeted individuals. Here's how hackers are weaponizing this flaw—and what you need to know to protect yourself.

The Vulnerability: A Hacker's Perfect Weapon
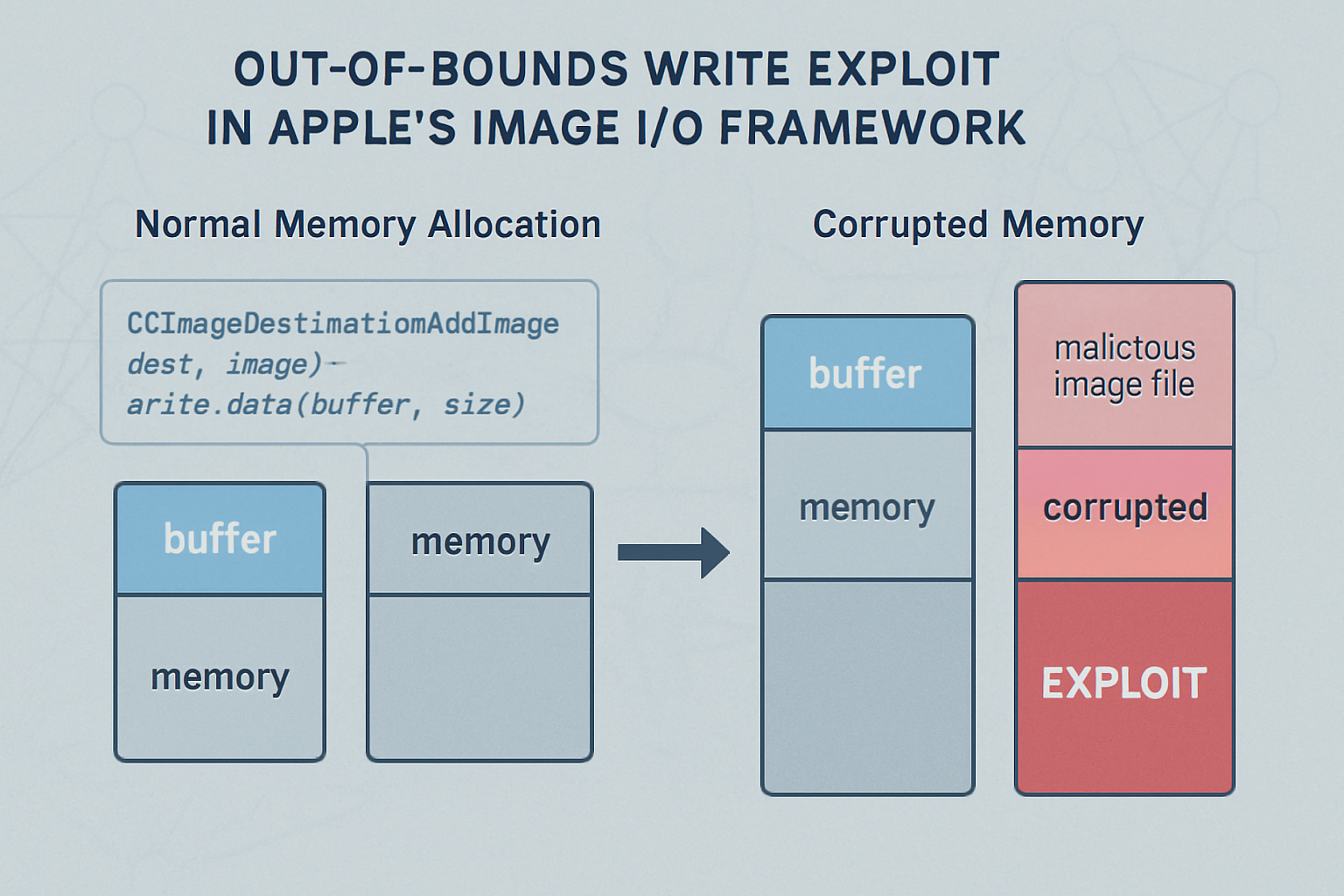
CVE-2025-43300 is an out-of-bounds write flaw in Apple's Image I/O framework—the system that processes every image on your iPhone, iPad, and Mac. What makes this vulnerability devastating is its simplicity: hackers only need to send you a malicious image file to completely compromise your device.
How the Attack Works
When you view a weaponized image, here's what happens in milliseconds:
- Malicious Image Processing: The crafted image triggers Apple's Image I/O framework to write data beyond allocated memory boundaries
- Memory Corruption: This overwrites critical system memory with attacker-controlled data
- Code Execution: The hacker gains the ability to run arbitrary code with application privileges
- Silent Compromise: Your device is compromised without any visible signs or user interaction
The scariest part? You don't need to download or save the image—simply viewing it in a web browser, email, or message is enough.
Reference: BleepingComputer: Apple fixes new zero-day flaw exploited in targeted attacks
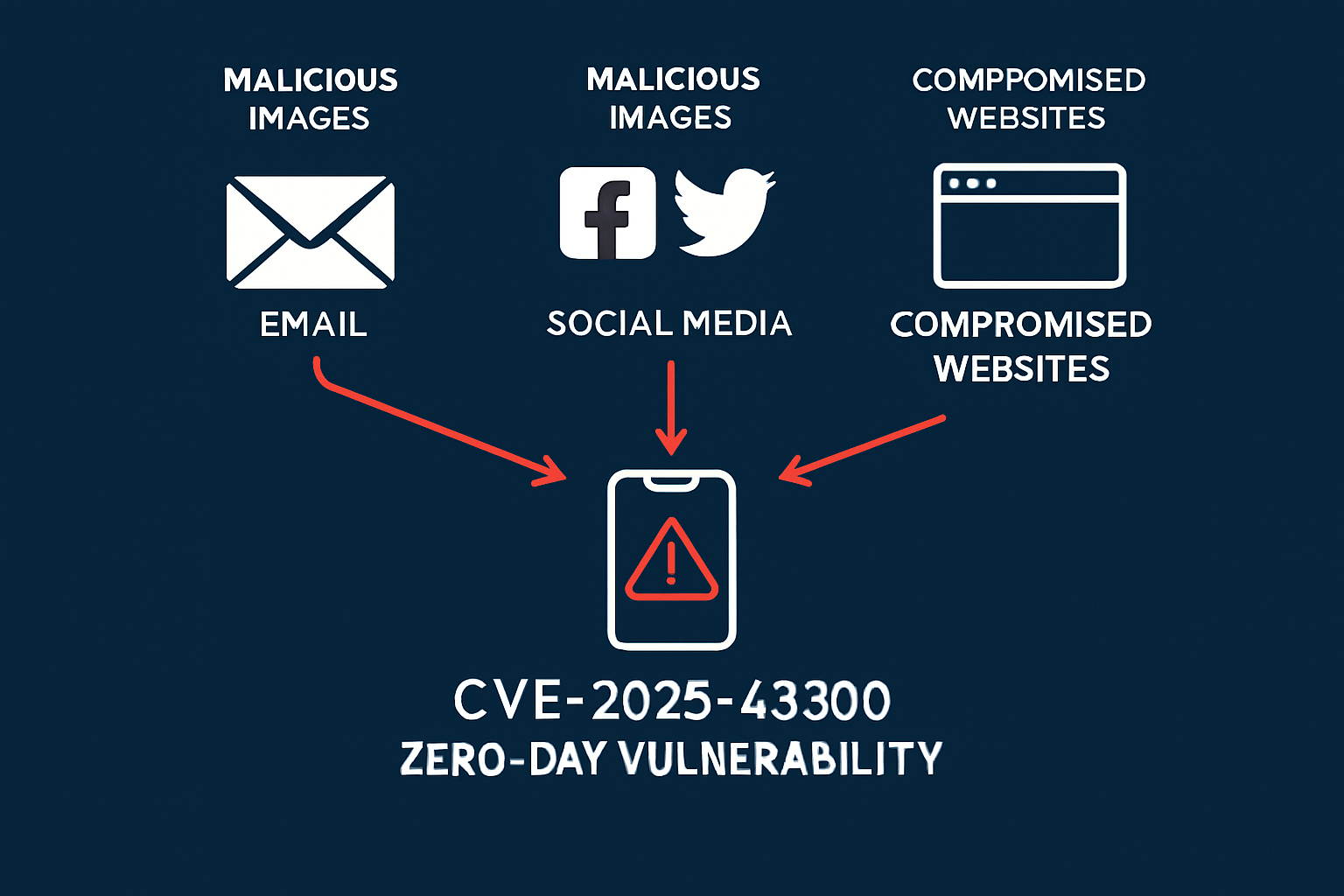
Real-World Attack Scenarios
The Executive Spear Phishing Campaign
Scenario: A Fortune 500 CEO receives an email with an "urgent contract review" containing a malicious image disguised as a company logo. The moment the email preview loads, the attacker gains access to the CEO's iPhone, potentially accessing:
- Corporate email and sensitive communications
- Banking and financial applications
- Executive calendar and meeting information
- Corporate VPN and internal systems access
The Social Media Trap
Scenario: Hackers upload weaponized images to social media platforms, LinkedIn profiles, or dating apps. When targets view these profiles, their devices become compromised instantly. This technique is particularly effective because:
- Users expect to see images on social platforms
- No suspicious download behavior is required
- Attacks appear to come from legitimate social media sources
The Web Watering Hole Attack
Scenario: Advanced persistent threat (APT) groups compromise legitimate websites frequented by their targets, injecting malicious images into web pages. Government officials, journalists, or corporate executives visiting these sites unknowingly trigger the exploit.
Why This Exploit is a Game-Changer
Massive Attack Surface
The vulnerability affects over 1.5 billion devices globally:
- iPhone XS and later (1.2+ billion devices)
- All modern iPads (300+ million devices)
- All recent Mac computers (100+ million devices)
No User Interaction Required
Unlike traditional malware that requires users to download and run files, CVE-2025-43300 exploitation is completely invisible:
- Images auto-load in email previews
- Web browsers automatically display images
- Messaging apps show image thumbnails
- No warning dialogs or suspicious prompts
Bypasses Traditional Security
This vulnerability defeats standard security measures:
- Antivirus software can't detect malicious images
- Firewalls allow normal image traffic
- User awareness training becomes irrelevant
- Email security gateways pass image attachments

The Sophisticated Attack Attribution
Apple's description of "extremely sophisticated attacks" suggests nation-state or advanced cybercriminal involvement. Security researchers believe this level of sophistication indicates:
Advanced Persistent Threat (APT) Characteristics:
- Targeted Operations: Attacks focused on specific high-value individuals rather than mass exploitation
- Stealth Capabilities: Operated undetected until Apple's security team discovered them
- Resource Investment: Zero-day discovery and weaponization requires significant technical expertise and funding
Likely Threat Actors:
- Nation-state intelligence agencies conducting espionage operations
- Advanced cybercriminal groups targeting executives and high-net-worth individuals
- Corporate espionage teams seeking competitive intelligence
The fact that this is Apple's sixth actively exploited zero-day in 2025 suggests coordinated efforts by multiple sophisticated adversaries.
Reference: CISA Known Exploited Vulnerabilities Catalog
Immediate Protection Steps
Critical Patches (Released August 20, 2025)
Update immediately to:
- iOS 18.6.2 and iPadOS 18.6.2 for latest devices
- macOS Sequoia 15.6.1 for newest Macs
- Legacy versions available for older supported devices
Emergency Defensive Measures
Until patching is complete:
- Disable automatic image loading in email clients
- Avoid clicking suspicious links or visiting untrusted websites
- Use corporate VPN for all internet access to add filtering layers
- Monitor devices for unusual behavior or battery drain
Detection Indicators
Signs your device may be compromised:
- Unusual network traffic or data usage
- Slower device performance or rapid battery drain
- Unexpected application behavior or crashes
- New files or applications appearing without installation
Why This Won't Be the Last
CVE-2025-43300 represents a new class of attack targeting fundamental system frameworks. Expect similar vulnerabilities to emerge in:
- Cross-platform image processing libraries (Windows, Android, Linux)
- Video processing frameworks using similar memory management
- Document rendering engines handling complex file formats
- IoT device media processing with limited security updates
The sophistication and success of this attack method will inspire copycat exploitation attempts across different platforms and frameworks.
Conclusion
CVE-2025-43300 demonstrates how sophisticated adversaries can weaponize basic system functions like image viewing into powerful attack vectors. The vulnerability's massive scope, minimal detection difficulty, and active exploitation by advanced threat actors make it one of 2025's most dangerous security threats.
The key takeaway: In the modern threat landscape, simply viewing an image can compromise your device. Traditional security awareness about "don't click suspicious links" becomes inadequate when the attack happens automatically through normal image viewing.
Immediate patching is non-negotiable. Organizations and individuals who delay updates expose themselves to invisible attacks that can provide persistent access to sensitive systems and data.
Your device could be compromised right now, and you'd never know it. Update immediately.
